The Evolving Landscape of Cyber Threats: Navigating the Risks of Internet Security in 2025
Related Articles: The Evolving Landscape of Cyber Threats: Navigating the Risks of Internet Security in 2025
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Evolving Landscape of Cyber Threats: Navigating the Risks of Internet Security in 2025. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Evolving Landscape of Cyber Threats: Navigating the Risks of Internet Security in 2025

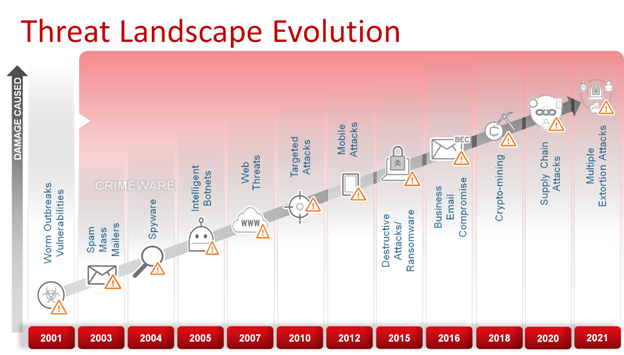
The internet, a vital tool for communication, commerce, and information access, is constantly evolving. This evolution brings advancements, but also presents new vulnerabilities. As technology progresses, so too do the methods and sophistication of cyber threats. Understanding the potential risks and implementing appropriate safeguards is crucial for individuals and organizations alike.
The Shifting Cyber Threat Landscape in 2025
Predictions for the future of cyber threats in 2025 point towards a landscape characterized by increased complexity and sophistication. Several key trends are expected to shape the threat environment:
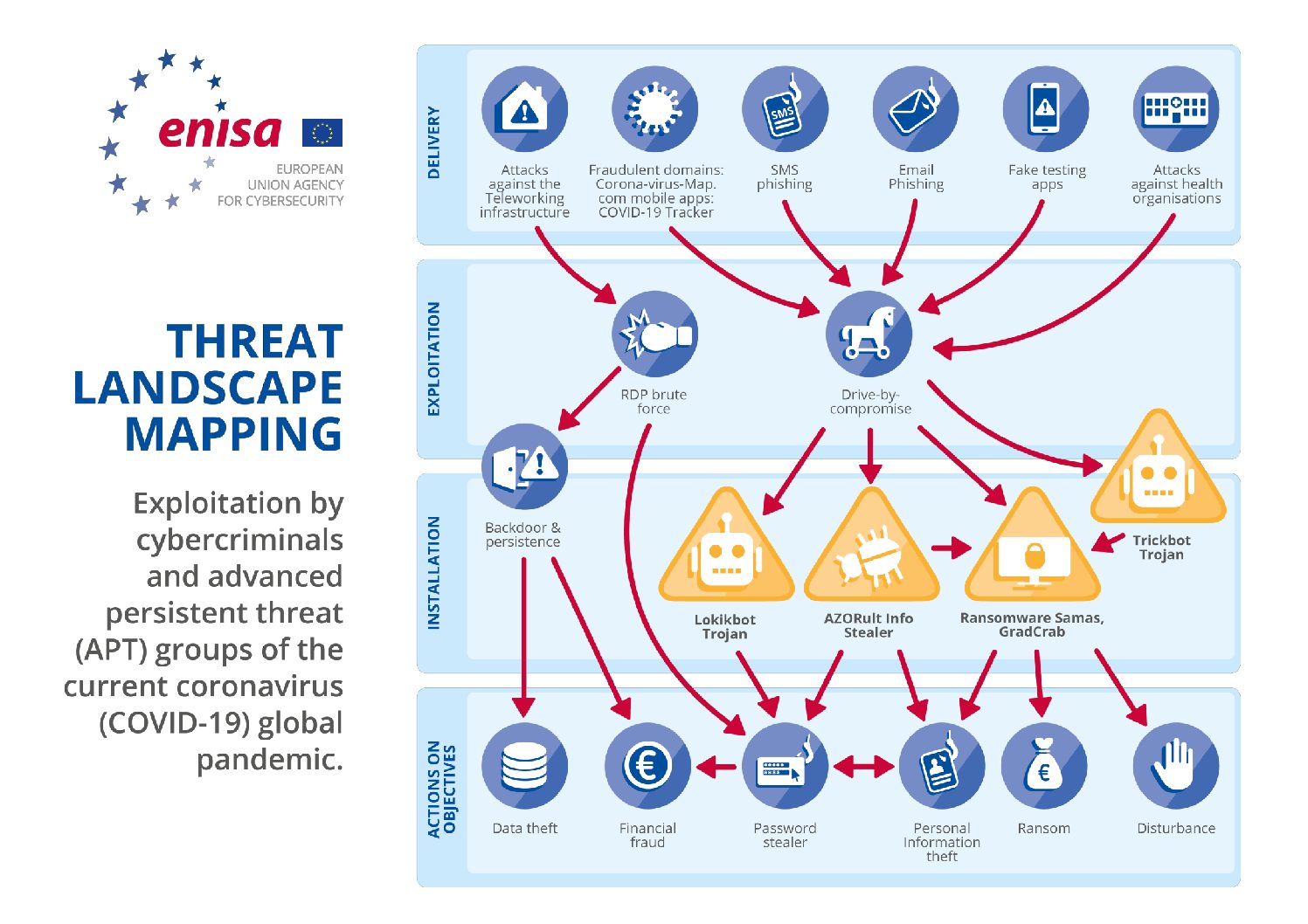
- Artificial Intelligence (AI) and Machine Learning (ML) in Cyberattacks: AI and ML are increasingly being used by malicious actors to automate and enhance their attacks. This includes developing more effective phishing campaigns, identifying vulnerabilities in systems, and even crafting custom malware.
- The Rise of Quantum Computing: The emergence of quantum computing poses a significant threat to current encryption methods. While still in its early stages, quantum computers have the potential to break the encryption algorithms used to secure sensitive data, potentially leading to widespread data breaches.
- The Internet of Things (IoT) as a New Attack Vector: The proliferation of interconnected devices, from smart homes to industrial equipment, creates a vast network of potential entry points for attackers. The inherent vulnerabilities in many IoT devices make them easy targets for exploitation.
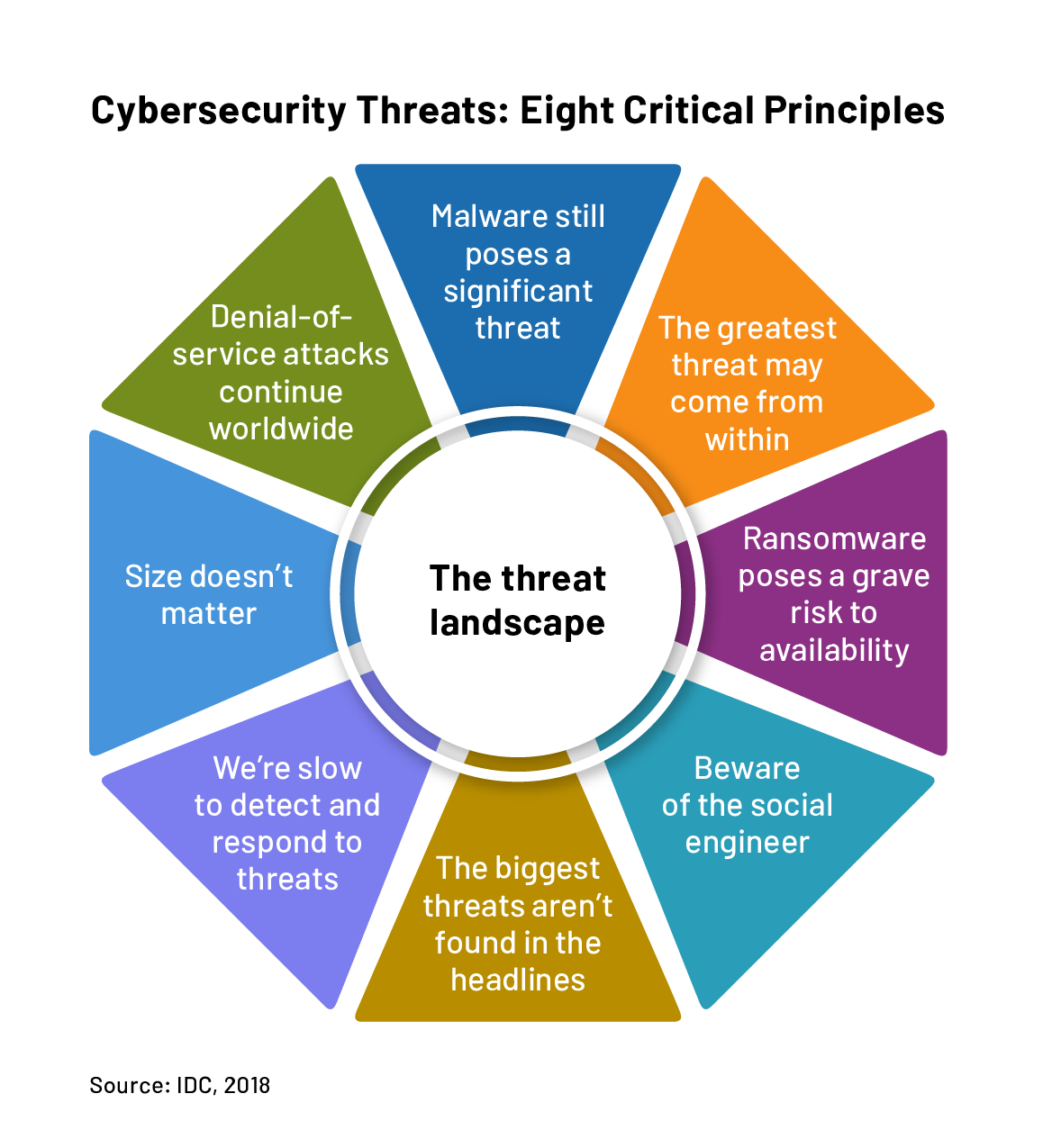
- The Growing Threat of Ransomware: Ransomware attacks, which encrypt data and demand payment for its release, have become increasingly prevalent and sophisticated.
- The Exploitation of Human Error: Cybercriminals continue to exploit human error as a primary attack vector. Phishing scams, social engineering techniques, and other methods that rely on user interaction remain effective in gaining access to sensitive information.
Understanding the Vulnerabilities: How Can Your Internet Be Compromised?
The internet, while offering unparalleled connectivity, is also inherently vulnerable. Several common methods used by cybercriminals to compromise systems include:
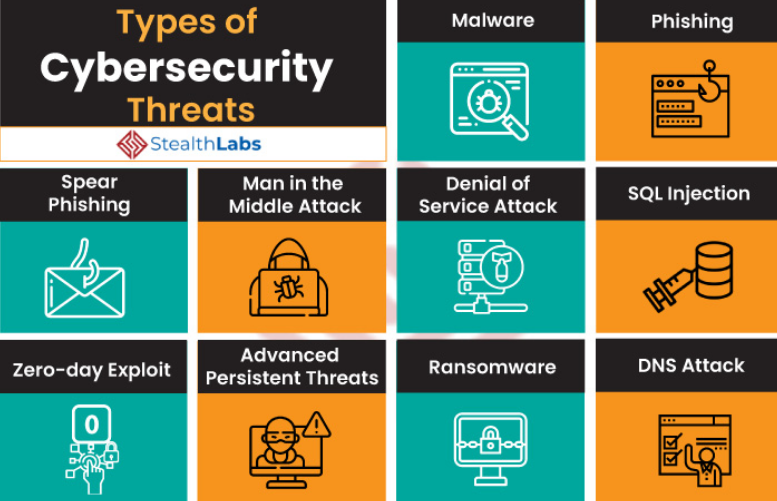
- Phishing: This involves sending emails or messages that appear legitimate but contain malicious links or attachments. Clicking on these links or opening attachments can install malware or grant access to personal information.
- Malware: Malicious software, or malware, can be installed on a device through various means, including phishing emails, infected websites, or compromised software. Malware can steal data, control the device, or provide access to attackers.
- Denial-of-Service (DoS) Attacks: These attacks attempt to overload a server or network with traffic, rendering it inaccessible to legitimate users.
- SQL Injection: This attack exploits vulnerabilities in web applications to gain unauthorized access to databases.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communication between two parties, potentially stealing sensitive information or altering data.
Protecting Your Internet: Essential Security Measures
While the threat landscape is constantly evolving, taking proactive steps to protect your internet connection and data remains crucial. Here are some essential security measures:
- Strong Passwords and Multi-Factor Authentication (MFA): Use strong, unique passwords for each online account and enable MFA whenever possible. MFA adds an extra layer of security by requiring an additional verification step, such as a code sent to your phone, before granting access.
- Regular Software Updates: Keeping software up to date is essential, as updates often include security patches that fix vulnerabilities.
- Antivirus and Firewall Software: Install and maintain reliable antivirus and firewall software to detect and block malware and unauthorized access.
- Secure Wi-Fi Networks: Use strong passwords for your home Wi-Fi network and avoid connecting to public Wi-Fi networks unless absolutely necessary.
- Be Aware of Phishing Scams: Be cautious of suspicious emails, messages, or phone calls. Never click on links or open attachments from unknown senders.
- Data Backups: Regularly back up important data to an external hard drive or cloud storage service. This helps to protect against data loss in the event of a cyberattack.
- Educate Yourself and Stay Informed: Keep abreast of the latest cyber threats and security best practices.
The Importance of a Proactive Approach
Cybersecurity is an ongoing process, not a one-time event. Staying vigilant and proactive in safeguarding your internet connection and data is essential. By understanding the evolving threat landscape, implementing appropriate security measures, and staying informed, individuals and organizations can mitigate the risks and navigate the digital world with greater confidence.
Frequently Asked Questions (FAQs)
Q: How can I tell if my internet connection has been compromised?
A: Signs of a compromised internet connection include:
- Unusual activity on your computer or devices: This could include slow performance, unexpected pop-ups, or programs launching without your permission.
- Changes in your network settings: If you notice changes in your Wi-Fi password or other network settings without making them yourself, it could be a sign of unauthorized access.
- Suspicious emails or messages: Be wary of emails or messages that ask for personal information, contain unusual links, or have grammatical errors.
- Unusual financial activity: If you notice unexplained charges on your credit card or bank account, it could be a sign of a data breach.
Q: What should I do if I suspect my internet connection has been compromised?
A: If you suspect your internet connection has been compromised, take the following steps:
- Disconnect from the internet: Immediately disconnect all devices from your network.
- Run a scan for malware: Use a reputable antivirus program to scan your devices for malware.
- Change your passwords: Change the passwords for all accounts that may have been compromised.
- Contact your internet service provider (ISP): Inform your ISP about the potential compromise and ask for assistance.
- Report the incident to the authorities: If you believe you have been the victim of a cybercrime, report it to the appropriate authorities.
Q: What are some tips for staying safe online?
A: Here are some additional tips for staying safe online:
- Use strong passwords: Create strong, unique passwords for each online account.
- Enable two-factor authentication (2FA): 2FA adds an extra layer of security by requiring a code sent to your phone before granting access.
- Be cautious of phishing emails: Don’t click on links or open attachments from unknown senders.
- Be aware of social engineering: Be cautious of requests for personal information, especially from unknown sources.
- Keep your software updated: Regularly update your operating system, web browser, and other software to patch vulnerabilities.
- Use a VPN: A VPN encrypts your internet traffic, making it more difficult for attackers to intercept your data.
Conclusion
The internet continues to evolve, and so too do the threats to its security. Staying informed about the latest cyber threats and implementing appropriate security measures is crucial for protecting your internet connection and data. By taking a proactive approach to cybersecurity, individuals and organizations can mitigate the risks and navigate the digital world with greater confidence. Remember, cybersecurity is an ongoing process, not a one-time event. Staying vigilant and adaptable is key to staying safe in the ever-changing digital landscape.



Closure
Thus, we hope this article has provided valuable insights into The Evolving Landscape of Cyber Threats: Navigating the Risks of Internet Security in 2025. We appreciate your attention to our article. See you in our next article!
